Introduction To Privileged Identity Management
In today’s fast changing digital landscape, it is critical to ensure the security and governance of your organization’s resources. A major component of this endeavour is managing and securing privileged identities.
Azure Privileged Identity Management (PIM) is a sophisticated Microsoft Azure service that assists enterprises in mitigating the risks associated with privileged access, improving security, and maintaining compliance. In this blog article, we will delve into Azure PIM, learning about its significance, features, and benefits, as well as how it can be used to improve your organization’s security posture.
Privileged Identity Management (PIM) Fundamentals
Privileged identities are user accounts with enhanced permissions that give access to sensitive resources within the environment of an organization. If these identities are compromised, they can result in catastrophic security breaches and unlawful access.
Privileged Identity Management (PIM) in Azure AD (Azure Active Directory) and other Microsoft Online Services is a comprehensive solution for managing, monitoring, and controlling privileged access.
Azure Devsecops Principles And Best Practices For Security In The Cloud
Azure PIM’s Key Features:
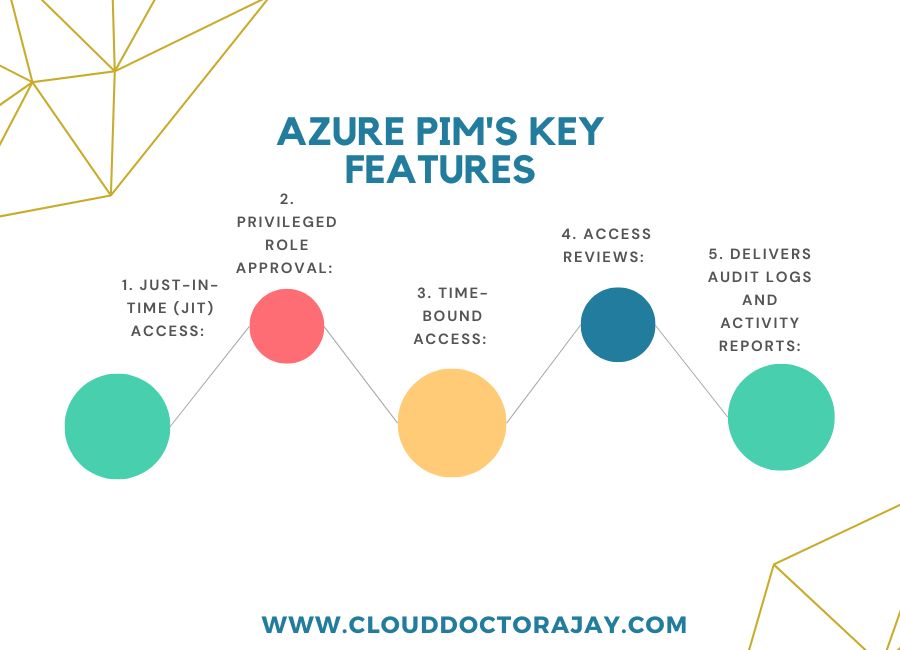
1. Just-In-Time (JIT) Access:
JIT access grants users temporary, time-bound privileged responsibilities only when they are required. This lessens the risk of illegal access and minimizes the exposure of critical resources.
2. Privileged Role Approval:
PIM offers a role approval procedure in which users can request privileged roles that designated approvers can grant or refuse. This provides an additional level of control and accountability.
3. Time-Bound Access:
Users assigned privileged roles via PIM are granted access for a set period of time. This ensures that rights are automatically withdrawn after a predetermined time period, decreasing the possibility of extended unwanted access.
4. Access Reviews:
Organizations can utilize regular access reviews to ensure that privileged positions are still essential and acceptable for individuals. This feature improves security by reevaluating access rights on a regular basis.
5. Delivers audit logs and activity reports:
PIM delivers extensive audit logs and activity reports, allowing organizations to track and analyse privileged access activities, assuring compliance and enabling rapid reaction to possible security breaches.
Introduction To Azure Security Architect Role & Responsibilities
Advantages of Azure PIM:
Check out most common advantages of Azure Privileged Identity Management
1. Reduced Attack Surface:
Azure PIM considerably limits the exposure of sensitive resources by offering temporary and time-bound access to privileged roles, making it more difficult for attackers to exploit them.
2. Increased Accountability:
Because access to privileged roles is subject to oversight and validation, role approval and access reviews encourage accountability within the business.
3. line and Auditing:
The strong auditing and reporting capabilities of Azure PIM assist enterprises in meeting regulatory requirements and remaining in line with industry standards.
4. Improved Incident reaction:
Detailed logs and activity reports allow for faster detection and reaction to suspicious actions, reducing the risk of security breaches.
5. Efficient Privilege Management:
Azure PIM streamlines privilege management operations with automated access assignment and revocation, minimizing administrative burden and human error.
5 Best Project Management Software In 2023
Implementing Azure PIM:
1. Assessment:
Identify the privileged identities and sensitive resources that need to be protected before implementing Azure PIM.
2. Configuration:
Create an Azure PIM instance, specify roles, approvers, and access controls in accordance with your organization’s requirements.
3. Role Activation:
Implement workflows for role approval and Just-In-Time access.
4. Access Reviews:
Review and recertify privileged jobs on a regular basis to make sure they remain necessary.
5. Monitoring:
Keep an eye out for any illegal or unusual attempts at access in audit logs and activity reports.
Conclusion:
Managing privileged identities is a key component of an organization’s cybersecurity strategy in a time when cyber threats are growing more complex. A wide range of capabilities and advantages provided by Azure Privileged Identity Management (PIM) enable enterprises to efficiently manage, secure, and govern privileged access.
Organizations may lower risks, improve accountability, manage compliance, and guarantee the security and integrity of their priceless digital assets by deploying Azure PIM. Adopting solutions like Azure PIM is crucial for protecting sensitive resources and keeping a solid security posture as the digital landscape changes constantly.